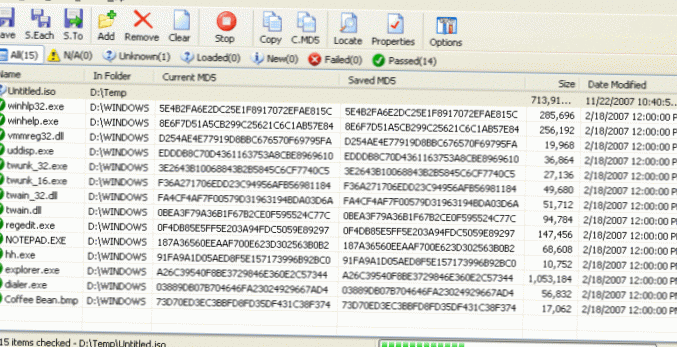
Hash Tool is a utility to calculate the hash of multiple files. A file hash can be said to be the 'signature' of a file and is used in many applications, including checking the integrity of downloaded files. This compact application helps you quickly and easily list the hashes of your files.
- How do I verify a hash file?
- What is MD5 check?
- How do I get an MD5 checksum?
- What is Hash validation?
- How do you generate a hash value?
- How do you use a hash algorithm?
- Why is MD5 bad?
- What is MD5 password?
- Why is MD5 weak?
- How do you find checksum?
- How do I run md5sum on Windows?
- What is the MD5 hash for the file provided?
How do I verify a hash file?
HashTab Hash Checker (Windows)
- Right-click the file on which you want to perform the MD5sum or hash value check.
- In the context menu, click on Properties > File Hashes.
- The tool will automatically list the hash value or checksum of CRC32, MD5, and SHA-1.
What is MD5 check?
An MD5 checksum is a 32-character hexadecimal number that is computed on a file. ... Use the computed MD5 checksum to compare against the MD5 checksum provided for that installation file on the download page. By doing this, you can verify the integrity of your download.
How do I get an MD5 checksum?
Open a terminal window. Type the following command: md5sum [type file name with extension here] [path of the file] -- NOTE: You can also drag the file to the terminal window instead of typing the full path. Hit the Enter key. You'll see the MD5 sum of the file.
What is Hash validation?
Hash-based verification ensures that a file has not been corrupted by comparing the file's hash value to a previously calculated value. If these values match, the file is presumed to be unmodified.
How do you generate a hash value?
Right-click on a file or a set of files, and click Hash with HashTools in the context menu. This launches the HashTools program and adds the selected file(s) to the list. Next, click on a hashing algorithm (e.g., CRC, MD5, SHA1, SHA256, etc) to generate the hash checksum for the files.
How do you use a hash algorithm?
Hashing Algorithm Explained
It is a mathematical algorithm that maps data of arbitrary size to a hash of a fixed size. A hash function algorithm is designed to be a one-way function, infeasible to invert. However, in recent years several hashing algorithms have been compromised.
Why is MD5 bad?
Using salted md5 for passwords is a bad idea. Not because of MD5's cryptographic weaknesses, but because it's fast. This means that an attacker can try billions of candidate passwords per second on a single GPU. What you should use are deliberately slow hash constructions, such as scrypt, bcrypt and PBKDF2.
What is MD5 password?
md5 (or better put: hash algorithms in general) are used to safely store passwords in database. ... A hash generates a fixed-length value from an arbitrary input (like a string), which can be used to see if the same input was used. Hashes are used to store sensitive, repeatly entered data in a storage device.
Why is MD5 weak?
The MD5 algorithm is reported prone to a hash collision weakness. This weakness reportedly allows attackers to create multiple, differing input sources that, when the MD5 algorithm is used, result in the same output fingerprint. ... Reportedly, at this time, attackers cannot generate arbitrary collisions.
How do you find checksum?
If m bit checksum is used, the data unit to be transmitted is divided into segments of m bits. All the m bit segments are added. The result of the sum is then complemented using 1's complement arithmetic. The value so obtained is called as checksum.
How do I run md5sum on Windows?
Verify the MD5 Checksum Using Windows
- Open Command Prompt.
- Open your downloads folder by typing cd Downloads. ...
- Type certutil -hashfile followed by the file name and then MD5.
- Check that the value returned matches the value the MD5 file you downloaded from the Bodhi website (and opened in Notepad).
What is the MD5 hash for the file provided?
MD5 is a one-way hash algorithm as defined by RFC1321 and can be used to help determine the integrity of a file by providing a 128 bit digital signature. This digital signature is like a fingerprint for a file; changing just one single byte in a file will result in a different MD5 hash.
 Naneedigital
Naneedigital