Simply open up Terminal, type md5sum filename.exe and it'll output the checksum value in Terminal. You can compare two checksum values by typing in two file names, like this: md5sum budget1.
- How do you verify data integrity?
- How do I check the integrity of an ISO file?
- Why is it a good idea to verify the hash of a file you had downloaded?
- What is integrity of message verification?
- What is data integrity with example?
- How do I know if my ISO is bootable?
- How do I know if ISO is corrupted?
- How do you check if Windows 10 ISO is corrupted?
- How do I verify a file checksum?
- How do I verify a hash file?
- How do I find the hash value of a file?
How do you verify data integrity?
Testing for Data Integrity
- A blank value can be retrieved from the database.
- Default values are saved if user input is not specified.
- Strings have been truncated or numeric values rounded.
- Removed records represent defunct, incorrect, or useless data.
- Third party data matches your existing data rules before importing.
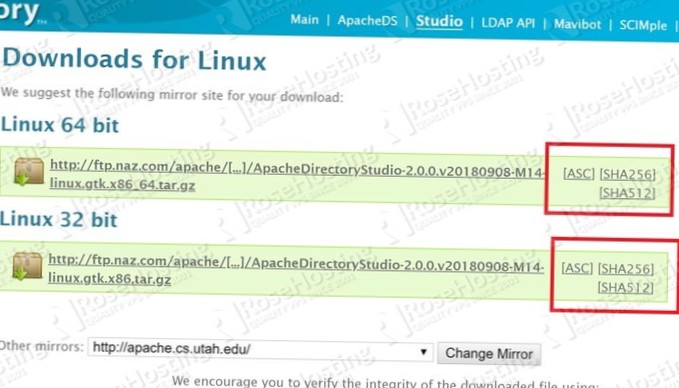
How do I check the integrity of an ISO file?
To verify the integrity of your ISO image, generate its SHA256 sum and compare it to the one found in the sha256sum. txt file. The last command should show you the SHA256 sum of your ISO file. Compare it to the one found in the sha256sum.
Why is it a good idea to verify the hash of a file you had downloaded?
A file can become corrupted by a variety of ways: faulty storage media, errors in transmission, write errors during copying or moving, software bugs, and so on. Hash-based verification ensures that a file has not been corrupted by comparing the file's hash value to a previously calculated value.
What is integrity of message verification?
Message Digest is used to ensure the integrity of a message transmitted over an insecure channel (where the content of the message can be changed). The message is passed through a Cryptographic hash function.
What is data integrity with example?
In its broadest use, “data integrity” refers to the accuracy and consistency of data stored in a database, data warehouse, data mart or other construct. ... As a simple example, to maintain data integrity numeric columns/cells should not accept alphabetic data.
How do I know if my ISO is bootable?
We will go step by step...
- By using PowerISO.
- First download and install PowerISO.
- Open PowerISO.
- Then click on FILE and then on OPEN and browse and open the ISO file.
- When you have opened that ISO file if that file is bootable then in the lower left end, it shows "Bootable image".
How do I know if ISO is corrupted?
Download pages also provide sha256sum digests for ISO images to verify against the file once it is downloaded. You can use sha256sum to generate the sha256 digest on your computer and verify it against the one available on the website. If they differ, then the downloaded ISO image is corrupt.
How do you check if Windows 10 ISO is corrupted?
Click File menu, click Open and browse to your Windows ISO file and click Open button. Step 3: Once the ISO file is loaded, you should see Bootable entry in the toolbar of MagicISO if the ISO is bootable (see picture).
How do I verify a file checksum?
WINDOWS:
- Download the latest version of WinMD5Free.
- Extract the downloaded zip and launch the WinMD5.exe file.
- Click on the Browse button, navigate to the file that you want to check and select it.
- Just as you select the file, the tool will show you its MD5 checksum.
How do I verify a hash file?
HashTab Hash Checker (Windows)
- Right-click the file on which you want to perform the MD5sum or hash value check.
- In the context menu, click on Properties > File Hashes.
- The tool will automatically list the hash value or checksum of CRC32, MD5, and SHA-1.
How do I find the hash value of a file?
Right-click on a file or a set of files, and click Hash with HashTools in the context menu. This launches the HashTools program and adds the selected file(s) to the list. Next, click on a hashing algorithm (e.g., CRC, MD5, SHA1, SHA256, etc) to generate the hash checksum for the files.
 Naneedigital
Naneedigital