Encryption
WEP, WPA, And WPA2 Protocols Comparison (Technical Differences)
While WEP uses simple PSK key, WPA and WPA2 combine it with other encryption methods like WPA-PSK and EAP-PSK to make the authentication process more ...
For Beginners What You Need to Know About Encryption on The Internet
How is encryption used on the Internet? What is the need for encryption? What is encryption in simple terms? Why is it important to encrypt data on th...
3 Reasons Why Encryption Is Not as Safe as You May Believe
What are the disadvantages of encryption? Why is encryption bad? What are the advantages and disadvantages of encryption? How safe is encryption? What...
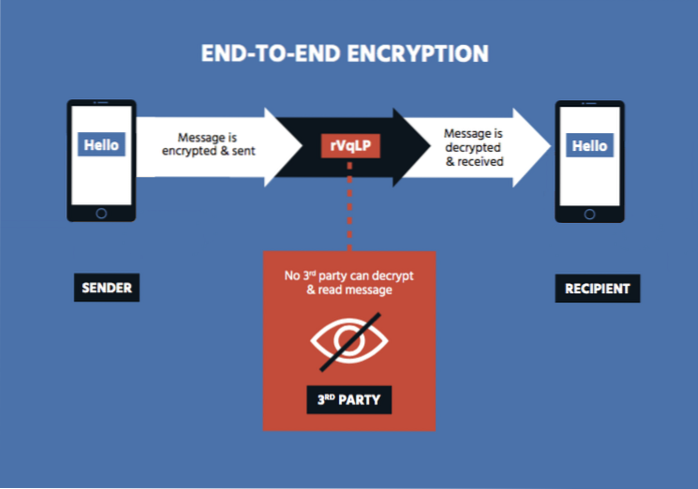
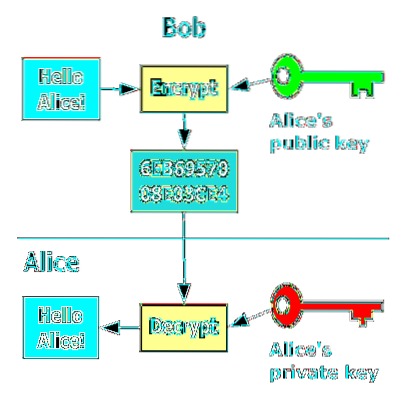
End-To-End Encryption (And Principle) Explained
End-to-end encryption is intended to prevent data being read or secretly modified, other than by the true sender and recipient(s). The messages are en...
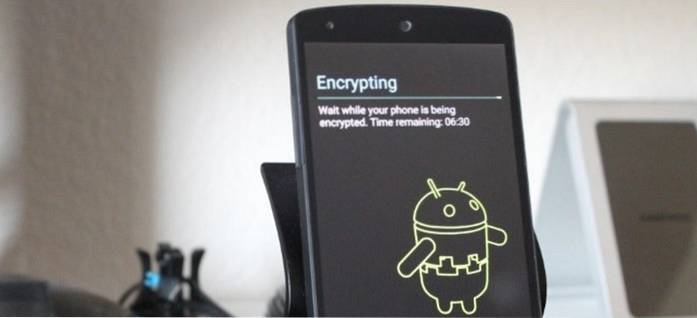
Do You Encrypt Your Smartphone?
How to encrypt your Android device. Plug in the device to charge the battery (required). Make sure a password or PIN is set in Security > Screen lo...
5 Ways to Encrypt Email for Linux
Yes, we're talking about encryption in email, on Linux specifically. ... Here are five ways you can encrypt your email on Linux. Enigmail for Thunderb...
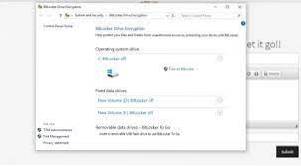
How to Perform Full-Disk Encryption in Windows 10
Turn on device encryption Sign in to Windows with an administrator account (you may have to sign out and back in to switch accounts). For more info, s...
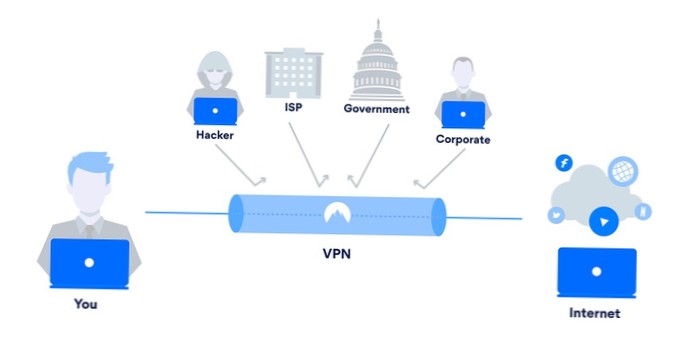
VPN Encryption Most Secure VPN Encryption Explained (Guide)
Which type of encryption is commonly used to secure VPNs? What is the most secure encryption algorithm? What are common VPN encryption protocols? What...
5 best Linux encryption tools to install
Here are the five best Linux encryption tools to install! ... Also, they have an exclusive offer for AddictiveTips readers 3 months free on the annual...
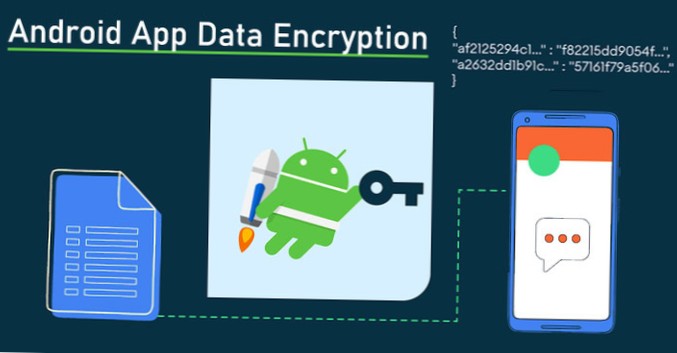
android encryption app
There are dedicated Android antivirus apps out there, as well as encrypted messaging apps for Android to help keep communications secure. ... ExpressV...
How Common Cryptography Techniques Work Online
How do we use cryptography today? What are the four 4 most secure encryption techniques? What are the most popular encryption systems used over the We...
Do You Think End-to-End Encryption Should Be Banned?
Is end to end encryption safe? Can End to end encryption be hacked? Is encryption good or bad? What is WND to end encryption? Can WhatsApp messages be...
 Naneedigital
Naneedigital