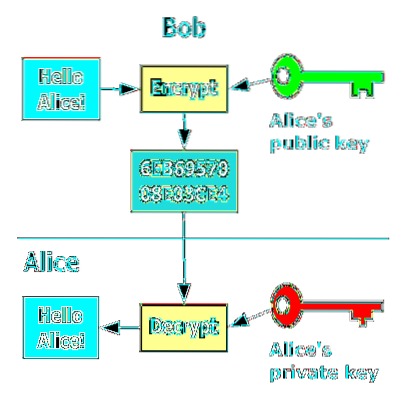
- How do we use cryptography today?
- What are the four 4 most secure encryption techniques?
- What are the most popular encryption systems used over the Web?
- What are the techniques of cryptography?
- What are the 3 main types of cryptographic algorithms?
- What are the two main types of cryptography?
- What is the hardest encryption to crack?
- What is the strongest encryption method?
- Which cryptography method is more secure?
- Which is better hashing or encryption?
- How do I know my encryption type?
- How can I make encryption more secure?
How do we use cryptography today?
Cryptography in Everyday Life
- Authentication/Digital Signatures. Authentication and digital signatures are a very important application of public-key cryptography. ...
- Time Stamping. ...
- Electronic Money. ...
- Secure Network Communications. ...
- Anonymous Remailers. ...
- Disk Encryption.
What are the four 4 most secure encryption techniques?
The 4 common encryption methods
- Advanced Encryption Standard (AES) Advanced Encryption Standard is a symmetric encryption algorithm that encrypts fixed blocks of data (of 128 bits) at a time. ...
- Rivest-Shamir-Adleman (RSA) ...
- Triple Data Encryption Standard (TripleDES) ...
- Twofish.
What are the most popular encryption systems used over the Web?
What are the most popular encryption systems used over the Web? The dominant Web encryption systems include SSL, 3DES, and PGP. Alternate answers could include RSA, AES, and RC6.
What are the techniques of cryptography?
In general there are three types Of cryptography:
- Symmetric Key Cryptography: It is an encryption system where the sender and receiver of message use a single common key to encrypt and decrypt messages. ...
- Hash Functions: There is no usage of any key in this algorithm. ...
- Asymmetric Key Cryptography:
What are the 3 main types of cryptographic algorithms?
There are three general classes of NIST-approved cryptographic algorithms, which are defined by the number or types of cryptographic keys that are used with each.
- Hash functions.
- Symmetric-key algorithms.
- Asymmetric-key algorithms.
- Hash Functions.
- Symmetric-Key Algorithms for Encryption and Decryption.
What are the two main types of cryptography?
There are two main types of cryptography systems : symmetric (" private key ") and asymmetric ( " public key " ).
What is the hardest encryption to crack?
Researchers crack the world's toughest encryption by listening to the tiny sounds made by your computer's CPU. Security researchers have successfully broken one of the most secure encryption algorithms, 4096-bit RSA, by listening — yes, with a microphone — to a computer as it decrypts some encrypted data.
What is the strongest encryption method?
The Advanced Encryption Standard (AES) is the algorithm trusted as the standard by the U.S. Government and numerous organizations. Although it is extremely efficient in 128-bit form, AES also uses keys of 192 and 256 bits for heavy duty encryption purposes.
Which cryptography method is more secure?
One of the most secure encryption types, Advanced Encryption Standard (AES) is used by governments and security organizations as well as everyday businesses for classified communications. AES uses “symmetric” key encryption. Someone on the receiving end of the data will need a key to decode it.
Which is better hashing or encryption?
Encryption is a two-way function; what is encrypted can be decrypted with the proper key. Hashing, however, is a one-way function that scrambles plain text to produce a unique message digest. With a properly designed algorithm, there is no way to reverse the hashing process to reveal the original password.
How do I know my encryption type?
Just put in a 17 character password and look at the length. If its 16 bytes you have MD5, 20 bytes means SHA-1, 24 bytes means DES or 3DES, 32 bytes means AES.
...
By far the most common schemes are:
- SHA-1 (160 bits)
- MD5 (128 bits)
- AES (128 bits)
- DES (64 bits)
- 3DES (64 bits)
How can I make encryption more secure?
Here are six tips for ensuring that encryption keeps you secure:
- Do Not Use Old Encryption Ciphers. ...
- Use Longest Encryption Keys You Can Support. ...
- Encrypt in Layers. ...
- Store Encryption Keys Securely. ...
- Ensure Encryption Implementation Is Done Right. ...
- Do Not Ignore External Factors.
 Naneedigital
Naneedigital