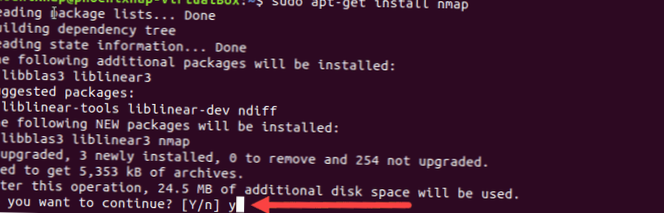
- Step 1: Update Ubuntu Package List. Make sure the software packages on your Ubuntu system are up-to-date with the command: sudo apt-get update. ...
- Step 2: Install Nmap. To install NMAP on Ubuntu, run the command: sudo apt-get install nmap. ...
- Step 3: Verify Nmap Version Installed.
- How do I start Nmap on Linux?
- How do I know if Nmap is installed on Linux?
- How install Nmap in Kali Linux?
- How do I get nmap?
- What does nmap do in Linux?
- How Hackers use open ports?
How do I start Nmap on Linux?
Install Nmap
- On CentOS. yum install nmap.
- On Debian. apt-get install nmap.
- On Ubuntu. sudo apt-get install nmap. Using the Nmap security scanner. Then you may run the command “nmap” on a terminal, accompanied by the target's IP or website address and the various available parameters.
How do I know if Nmap is installed on Linux?
To test the currently installed version of NMAP use the command 'nmap --version'. If you are moving to version 7.40 that should be fine, but some screen shots may differ. NOTE: You can also test the other utilities with the option '--version' after the utility name.
How install Nmap in Kali Linux?
Open a terminal in Kali Linux and type, git clone https://github.com/nmap/nmap.git to begin the cloning process. After this command is entered, the tool will be downloaded and installed automatically. After the install is complete, you will need to confirm that you are using the latest version of Nmap.
How do I get nmap?
Browse to https://nmap.org/download.html and download the latest self-installer:
- Run the downloaded .exe file. In the window that opens, accept the license terms:
- Choose the components to install. ...
- Select the install location and click Install:
- The installation should be completed in a couple of minutes.
What does nmap do in Linux?
Nmap, or Network Mapper, is an open source Linux command line tool for network exploration and security auditing. With Nmap, server administrators can quickly reveal hosts and services, search for security issues, and scan for open ports.
How Hackers use open ports?
Malicious ("black hat") hackers (or crackers) commonly use port scanning software to find which ports are "open" (unfiltered) in a given computer, and whether or not an actual service is listening on that port. They can then attempt to exploit potential vulnerabilities in any services they find.
 Naneedigital
Naneedigital