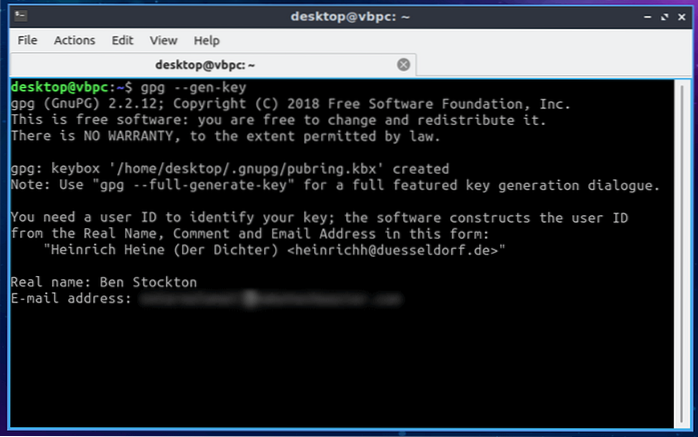
To generate a key:
- Open a terminal and enter: gpg --gen-key. ...
- Enter the keysize. ...
- Specify how long the key should be valid for. ...
- Hit Y to confirm. ...
- Enter real name, comment, and email address when prompted. ...
- Type O to continue. ...
- Enter your passphrase twice.
- How do I create a GPG key?
- How do I generate a PGP key in Linux?
- How do I find my GPG key in Linux?
- How can I get GPG public key?
- What is GPG secret key?
- How does GPG key work?
- How do I decode a PGP message?
- What are GPG keys in Linux?
- How do I find my fingerprint PGP key?
- How do I trust a GPG key?
- Where are RPM GPG keys stored?
- What is RPM key?
How do I create a GPG key?
Generating a GPG key
- Download and install the GPG command line tools for your operating system. ...
- Open .
- Generate a GPG key pair. ...
- At the prompt, specify the kind of key you want, or press Enter to accept the default RSA and RSA .
- Enter the desired key size. ...
- Enter the length of time the key should be valid.
How do I generate a PGP key in Linux?
Generate A Key Pair
- Open a command shell or DOS prompt.
- On the command line, enter: pgp --gen-key [user ID] --key-type [key type] --bits [bits #] --passphrase [passphrase] ...
- Press "Enter" when the command is complete. ...
- PGP Command line will now generate your keypair.
How do I find my GPG key in Linux?
Open . Use the gpg --list-secret-keys --keyid-format LONG command to list GPG keys for which you have both a public and private key.
How can I get GPG public key?
How to Generate a Public-Private Key Pair
- Generate a new keypair: gpg --gen-key.
- Export the keypair to a file (use the same email address that you used for generating the key pair): gpg --export -a "[email protected]" > public.key.
- Download the GoodData public PGP key.
- Import the GoodData public key to your keystore: gpg --import gooddata-sso.pub.
What is GPG secret key?
gpg --export-secret-key -a "User Name" > private.key. This will create a file called private. key with the ascii representation of the private key for User Name. It's pretty much like exporting a public key, but you have to override some default protections.
How does GPG key work?
GPG uses a method of encryption known as public key (asymmetric) cryptography, which provides a number of advantages and benefits. In a public key (asymmetric) encryption system, any person can encrypt a message using a public key. That encrypted message can only be decrypted with the corresponding private key.
How do I decode a PGP message?
Decrypt messages
- Open the e-mail containing the encrypted message in ciphertext.
- Highlight the block of ciphertext.
- Open the PGP Tray.
- Select Current Window. Choose Decrypt & Verify.
- Enter a passphrase into the PGP Enter Passphrase dialog box. Click OK.
- The decrypted message will come up in a new window for you to read.
What are GPG keys in Linux?
GnuPG uses public-key cryptography so that users may communicate securely. In a public-key system, each user has a pair of keys consisting of a private key and a public key. A user's private key is kept secret; it need never be revealed. The public key may be given to anyone with whom the user wants to communicate.
How do I find my fingerprint PGP key?
How to Generate PGP Keys
- Initialize the GPG Directory. > gpg --gen-key. gpg (GnuPG) 1.0. ...
- Generate a Private Key. > gpg --gen-key. ...
- Generate and print a copy of your public key ID and fingerprint >gpg --fingerprint. An an example of the fingerprint output, here is the output of the NMLUG Keymaster's fingerprint:
How do I trust a GPG key?
At the gpg> prompt, type trust , then type 5 for ultimate trust, then y to confirm, then quit .
Where are RPM GPG keys stored?
3 Answers. It's stored in the rpmdb, with the name of gpg-pubkey and the version as the first 8 hexadecimal characters of the fingerprint.
What is RPM key?
The rpm utility uses GPG keys to sign packages and its own collection of imported public keys to verify the packages. YUM and DNF use repository configuration files to provide pointers to the GPG public key locations and assist in importing the keys so that RPM can verify the packages.
 Naneedigital
Naneedigital