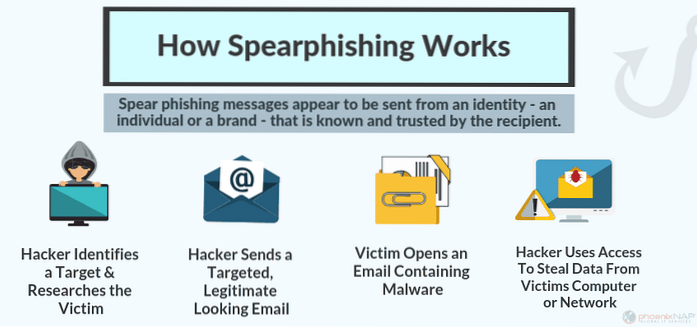
Spear phishing is an email or electronic communications scam targeted towards a specific individual, organization or business. ... This is how it works: An email arrives, apparently from a trustworthy source, but instead it leads the unknowing recipient to a bogus website full of malware.
- Is spearfishing a highly targeted phishing attempt?
- How do phishers target their victims?
- What is a typical spear phishing attempt?
- Why is spear phishing so difficult to detect?
- Why is phishing so dangerous?
- What are examples of phishing?
- What are 2 types of phishing?
- How do you know if you've been phished?
- What happens when you get phished?
- What are the 2 most common types of phishing attacks?
- What helps to protect from spear phishing?
- What is difference between phishing and spear phishing?
Is spearfishing a highly targeted phishing attempt?
Spear phishing is a very common form of attack on businesses too. Because it's so targeted, spear phishing is arguably the most dangerous type of phishing attack. According to Proofpoint's 2020 State of the Phish (PDF) report, 65 percent of US businesses were victims of successful phishing attacks in 2019.
How do phishers target their victims?
When attackers try to craft a message to appeal to a specific individual, that's called spear phishing. ... Phishers identify their targets (sometimes using information on sites like LinkedIn) and use spoofed addresses to send emails that could plausibly look like they're coming from co-workers.
What is a typical spear phishing attempt?
Spear phishing is a phishing method that targets specific individuals or groups within an organization. ... A typical spear phishing attack includes an email and attachment. The email includes information specific to the target, including the target's name and rank within the company.
Why is spear phishing so difficult to detect?
Because of the personal level of these emails, it is more difficult to identify spear-phishing attacks than to identify phishing attacks conducted at a wide scale. This is why spear-phishing attacks are becoming more prevalent.
Why is phishing so dangerous?
Phishing is one of the most dangerous threats to your online accounts and data, because these kind of exploits hide behind the guise of being from a reputable company or person, and use elements of social engineering to make victims far more likely to fall for the scam.
What are examples of phishing?
Examples of Different Types of Phishing Attacks
- Phishing Email. Phishing emails still comprise a large portion of the world's yearly slate of devastating data breaches. ...
- Spear Phishing. ...
- Link Manipulation. ...
- Fake Websites. ...
- CEO Fraud. ...
- Content Injection. ...
- Session Hijacking. ...
- Malware.
What are 2 types of phishing?
What are the different types of phishing?
- Spear phishing.
- Whaling.
- Vishing.
- Email phishing.
How do you know if you've been phished?
6 sure signs someone is phishing you—besides email
- Your software or app itself is phishing. ...
- You've received a mysterious text or call. ...
- You've “won” something. ...
- Your social media accounts are being weaponized. ...
- Your URL doesn't look right. ...
- You've been warned or given an ultimatum.
What happens when you get phished?
Phishing schemes are a type of scam in which cybercriminals attempt to gain access to your sensitive data. ... If you don't realize the email is fraudulent, you may end up following the instructions in the email and reveal your passwords, credit card information, or Social Security number.
What are the 2 most common types of phishing attacks?
6 Common Phishing Attacks and How to Protect Against Them
- Deceptive Phishing. Deceptive phishing is by far the most common type of phishing scam. ...
- Spear Phishing. Not all phishing scams embrace “spray and pray” techniques. ...
- CEO Fraud. Spear phishers can target anyone in an organization, even executives. ...
- Vishing. ...
- Smishing. ...
- Pharming.
What helps to protect from spear phishing?
How to Protect Yourself against Spear Phishing
- Keep your systems up-to-date with the latest security patches. ...
- Encrypt any sensitive company information you have. ...
- Use DMARC technology. ...
- Implement multi-factor authentication wherever possible. ...
- Make cybersecurity a company focus.
What is difference between phishing and spear phishing?
Phishing and spear phishing are very common forms of email attack designed to you into performing a specific action—typically clicking on a malicious link or attachment. The difference between them is primarily a matter of targeting. ... Spear phishing emails are carefully designed to get a single recipient to respond.
 Naneedigital
Naneedigital