Five Ways to Protect Yourself:
- Delete any request for personal information or passwords. Nobody should be contacting you for your personal information via email unsolicitedly. ...
- Reject requests for help or offers of help. ...
- Set your spam filters to high. ...
- Secure your devices. ...
- Always be mindful of risks.
- What is a social engineering attack and how can it be prevented?
- What are three techniques used in social engineering attacks?
- What are social engineering tactics?
- Which of the following is a way to protect against social engineering?
- What is your best defense against social engineering attacks?
- What is the most common form of social engineering?
- What are the six types of social engineering?
- How do hackers use social engineering?
- What is social engineering attack called?
- What does a social engineering attack look like?
- What is social engineering and its types?
- What is a common method used in social engineering cyber awareness?
What is a social engineering attack and how can it be prevented?
You have some website or something you sent directly to the target, prompting them to enter their credentials. When they do so, their credentials are sent to the attacker. Preventing this attack is as simple as not entering your credentials into anything you don't trust or expect.
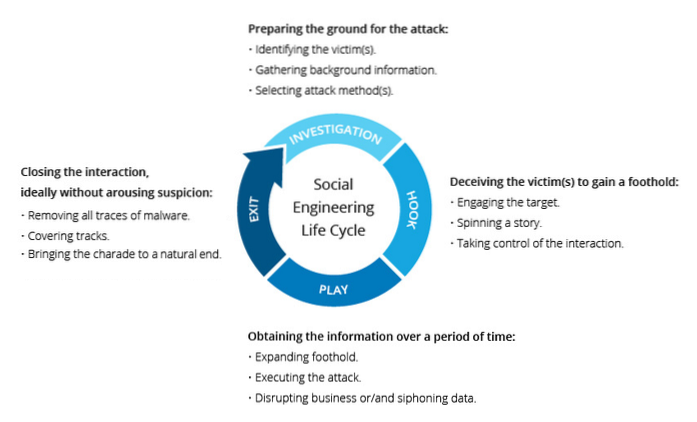
What are three techniques used in social engineering attacks?
Social engineering attack techniques
- Baiting. As its name implies, baiting attacks use a false promise to pique a victim's greed or curiosity. ...
- Scareware. Scareware involves victims being bombarded with false alarms and fictitious threats. ...
- Pretexting. Here an attacker obtains information through a series of cleverly crafted lies. ...
- Phishing. ...
- Spear phishing.
What are social engineering tactics?
Examples & Prevention Tips
Social engineering is the art of manipulating people so they give up confidential information. ... Criminals use social engineering tactics because it is usually easier to exploit your natural inclination to trust than it is to discover ways to hack your software.
Which of the following is a way to protect against social engineering?
The best defense against social engineering attacks is a comprehensive training and awareness program that includes social engineering. The training should emphasize the value of being helpful and working as a team, but doing so in an environment where trust is verified and is a ritual without social stigma.
What is your best defense against social engineering attacks?
To avoid becoming a victim of a social engineering attack: Be suspicious of unsolicited contacted from individuals seeking internal organizational data or personal information. Do not provide personal information or passwords over email or on the phone. Do not provide information about your organization.
What is the most common form of social engineering?
The most common form of social engineering attack is phishing. Phishing attacks exploit human error to harvest credentials or spread malware, usually via infected email attachments or links to malicious websites.
What are the six types of social engineering?
So, let's tell you about different types of social engineering attacks:
- Phishing. Phishing is the most common type of social engineering attack. ...
- Spear Phishing. A social engineering technique known as Spear Phishing can be assumed as a subset of Phishing. ...
- Vishing. ...
- Pretexting. ...
- Baiting. ...
- Tailgating. ...
- Quid pro quo.
How do hackers use social engineering?
Social engineering is all about manipulating individuals on an interpersonal level. It involves the hacker trying to gain their victim's trust and persuade them to reveal confidential information, for example, or to share credit card details and passwords.
What is social engineering attack called?
Phishing attacks
Phishing is a leading form of social engineering attack that is typically delivered in the form of an email, chat, web ad or website that has been designed to impersonate a real system, person, or organization.
What does a social engineering attack look like?
Examples of social engineering range from phishing attacks where victims are tricked into providing confidential information, vishing attacks where an urgent and official sounding voice mail convinces victims to act quickly or suffer severe consequences, or physical tailgating attacks that rely on trust to gain ...
What is social engineering and its types?
Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables. In cybercrime, these “human hacking” scams tend to lure unsuspecting users into exposing data, spreading malware infections, or giving access to restricted systems.
What is a common method used in social engineering cyber awareness?
Phishing. Phishing attacks are the most common type of attacks leveraging social engineering techniques. Attackers use emails, social media, instant messaging and SMS to trick victims into providing sensitive information or visiting malicious URLs in the attempt to compromise their systems.
 Naneedigital
Naneedigital