10 Steps to Secure Open SSH
- Strong Usernames and Passwords. ...
- Configure Idle Timeout Interval. ...
- Disable Empty Passwords. ...
- Limit Users' SSH Access. ...
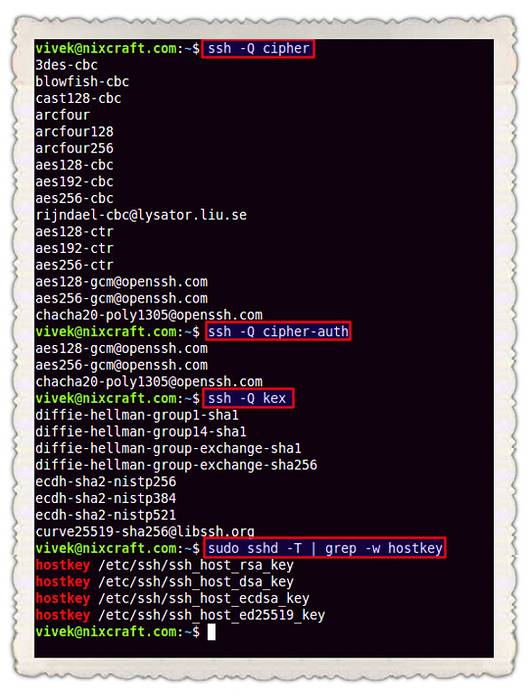
- Only Use SSH Protocol 2. ...
- Allow Only Specific Clients. ...
- Enable Two-Factor Authentication. ...
- Use Public/Private Keys for Authentication.
- Why is SSH bad?
- Is open SSH safe?
- How do I harden SSH server?
- What is remote SSH?
- Is SSH secure enough?
- What happens when port 22 opens?
- Is SSH hack possible?
- What port should I use for SSH?
- Is port 22 secure?
- How do I harden SSH in Ubuntu?
- How do I harden Ubuntu 18.04 Server?
- What is the use of OpenSSH?
Why is SSH bad?
Careless Users: When users are authorized to use SSH public key authentication, they can be careless in their handling of their private keys, either placing them in insecure locations, copying them to multiple computers, and not protecting them with strong passwords.
Is open SSH safe?
OpenSSH is the standard for secure remote access to *Unix-like servers, replacing the unencrypted telnet protocol. SSH (and its file transfer sub-protocol SCP) ensures that the connection from your local computer to the server is encrypted and secure.
How do I harden SSH server?
- Set idle timeout interval. The idle timeout interval is is the amount of time in which an ssh session is allowed to sit idle. ...
- Disable empty passwords. There are some system user accounts that are created without passwords. ...
- Disable X11 forwarding. ...
- Limit max authentication attempts. ...
- Disable SSH on desktops.
What is remote SSH?
Remote SSH is a little helper tool originally for Windows to quickly start Putty and connect to a potential server you are currently working on. While the default SSH client is Putty, Remote SSH supports the default SSH client of Linux and Mac, or any other ssh client called ssh that is globally accessible, too.
Is SSH secure enough?
If you are using public key authentication for SSH, no one can log in to the server without having the corresponding private key. This is as secure, and usually more secure, than password authentication. The encryption OpenSSH provides is state of the art; there is no known way to break it.
What happens when port 22 opens?
If you have port 22 open and an SSH daemon running on it, you'll likely see 100s if not 1000s or more attempts to login every day. Probably for the most part, “kiddie-scripts” testing for default or common login / passwords. A total waste of your server resources, and a huge security risk.
Is SSH hack possible?
SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials.
What port should I use for SSH?
The default port for SSH client connections is 22; to change this default, enter a port number between 1024 and 32,767. The default port for Telnet client connections is 23; to change this default, enter a port number between 1024 and 32,767.
Is port 22 secure?
Avoid Port 22
Port 22 is the standard port for SSH connections. If you use a different port, it adds a little bit of security through obscurity to your system. Security through obscurity is never considered a true security measure, and I have railed against it in other articles.
How do I harden SSH in Ubuntu?
Secure the SSH server on Ubuntu
- Change the default SSH port.
- Use SSH2.
- Use a whitelist and a blacklist to limit user access.
- Disable root login.
- Hide last login.
- Restrict SSH logins to specific IP addresses.
- Disable password authentication.
- Disable .rhosts.
How do I harden Ubuntu 18.04 Server?
The following tips and tricks are some easy ways to quickly harden an Ubuntu server.
- Keep System Up-To-Date. ...
- Accounts. ...
- Ensure Only root Has UID of 0. ...
- Check for Accounts with Empty Passwords. ...
- Lock Accounts. ...
- Adding New User Accounts. ...
- Sudo Configuration. ...
- IpTables.
What is the use of OpenSSH?
OpenSSH is a freely available version of the Secure Shell (SSH) protocol family of tools for remotely controlling, or transferring files between, computers. Traditional tools used to accomplish these functions, such as telnet or rcp, are insecure and transmit the user's password in cleartext when used.
 Naneedigital
Naneedigital