Ms. Johnny Upton, articles - page 116
How to Use the ZFS Filesystem on Ubuntu Linux
How do I mount a ZFS file system in Ubuntu? Does Linux support ZFS? How do I mount a ZFS file system in Linux? Should I use ZFS Ubuntu? What is ZFS in...
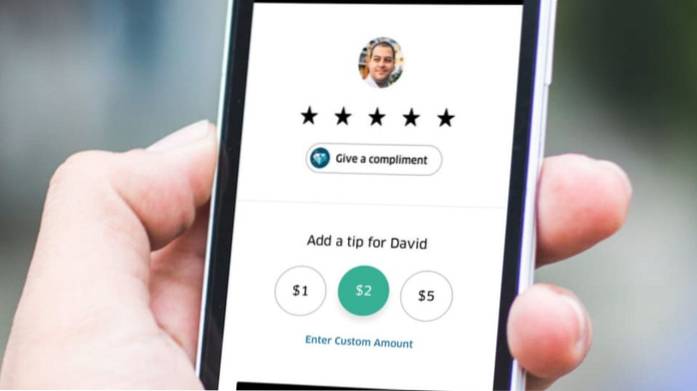
5 Uber Tips
How to maintain your 5-star Uber driver rating? Have a smooth ride. One of the most important factors to becoming a 5-star Uber driver is the quality ...
What Happens When You Restart Your Computer
Flushes RAM – RAM stands for Random Access Memory and is your computer's main type of memory. It's also known as volatile memory because it is constan...
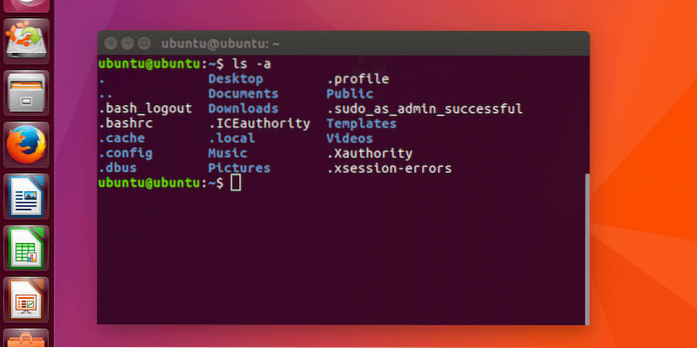
What Are the Hidden Files in my Linux Home Directory For?
In most cases the hidden files in your Linux home directory as used to store user settings. This includes settings for command-line utilities as well ...
What “Malvertising” Is, How It Affects You and How to Stop It
How do I get rid of malvertising? What is a malvertising attack? Can ads give you a virus? Are ads Dangerous? How do I remove malware manually? How ca...
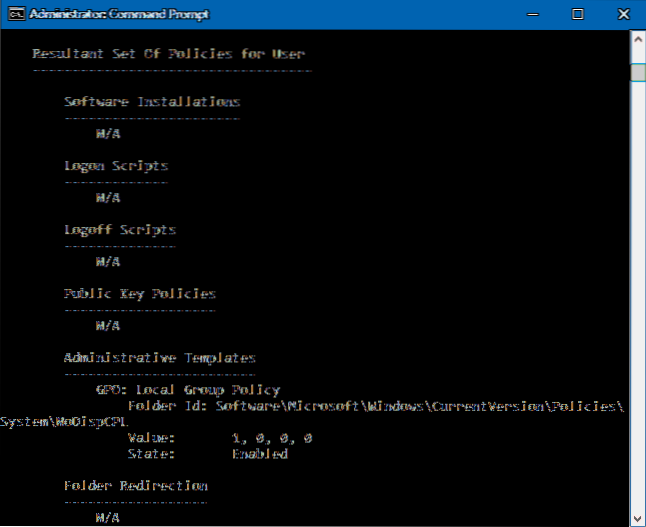
How to See All the Group Policies Applied to Windows
How to View Group Policy Applied to Your Windows 10 User Press the Windows key + R to open the Run box. Type rsop. msc and press Enter. The Resultant ...
How to Edit the Context Menu in macOS
How to Customize the macOS Context Menu Click on the Apple menu and open the System Preferences application. ... Open the Keyboard preference pane. Cl...
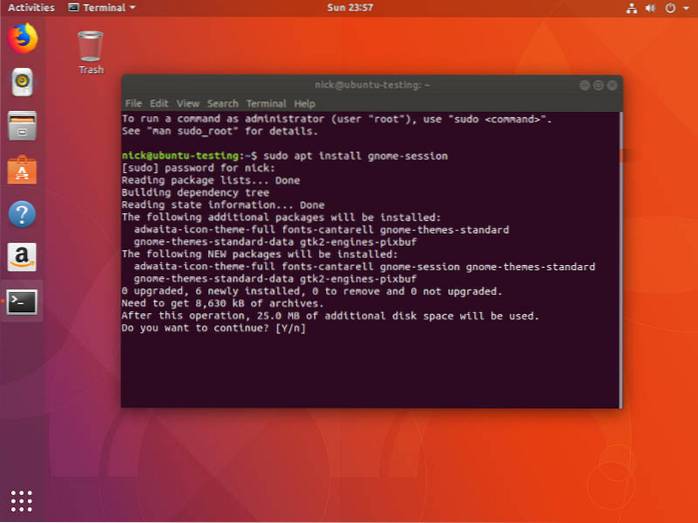
How to Get Vanilla GNOME Shell in Ubuntu
How to install Vanilla Gnome on Ubuntu 18.04 Open a Terminal window. Install gnome-sessions sudo apt install gnome-session. Enter 'Y' to install the r...
14 Ways to Make Good Use of Your Old Computer Again
14 Ways to Make Good Use of Your Old Computer Again Create a Digital Photoframe ... An External Portable Storage. ... A Second Display. ... Sell It to...
What Are “Loot Boxes” in Games, and Why Are They Controversial?
What's wrong with loot boxes? What is a loot box in gaming? What is game loot? Why should loot boxes be banned? What's wrong with loot boxes? The link...
Why Do Executives Hide Data Breaches?
They hide data breaches because they can. There is no accountability in tech. If you can concentrate user data into select DBs instead of spreading it...
6 of the Best ISO Mounting Software for All Platforms
What is the best ISO mounting software? What software can I use to mount an ISO file? Can Windows 7 mount ISO natively? What is ISO mounting software?...
 Naneedigital
Naneedigital