- Why SHA1 is not secure?
- Is SHA-1 broken?
- Is SHA1 still secure?
- Is SHA1 deprecated?
- Which SHA is most secure?
- What hashing means?
- Is SHA256 Crackable?
- Which is faster MD5 or SHA1?
- What is hash coding?
- Is SHA512 better than SHA256?
- Which is better SHA1 or SHA256?
- Which hashing algorithm is the least secure?
Why SHA1 is not secure?
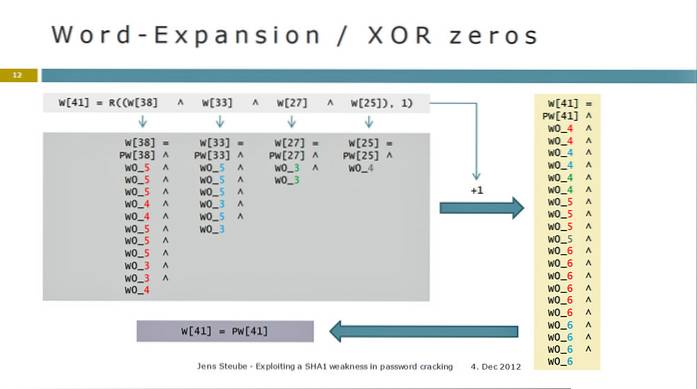
It is supposed to be unique and non-reversible. If a weakness is found in a hash function that allows for two files to have the same digest, the function is considered cryptographically broken, because digital fingerprints generated with it can be forged and cannot be trusted.
Is SHA-1 broken?
UPDATE--SHA-1, the 25-year-old hash function designed by the NSA and considered unsafe for most uses for the last 15 years, has now been “fully and practically broken” by a team that has developed a chosen-prefix collision for it.
Is SHA1 still secure?
All major web browser vendors ceased acceptance of SHA-1 SSL certificates in 2017. In February 2017, CWI Amsterdam and Google announced they had performed a collision attack against SHA-1, publishing two dissimilar PDF files which produced the same SHA-1 hash. But SHA-1 is still secure for HMAC.
Is SHA1 deprecated?
In response to rising concerns, the NIST (National Institute of Standards and Technology) officially deprecated SHA-1 in 2011. Most recently, on February 23rd, 2017, Google and the Dutch research institute CWI announced that they successfully broke SHA-1 n practice using a simulated collision attack.
Which SHA is most secure?
The SHA-256 algorithm returns hash value of 256-bits, or 64 hexadecimal digits. While not quite perfect, current research indicates it is considerably more secure than either MD5 or SHA-1. Performance-wise, a SHA-256 hash is about 20-30% slower to calculate than either MD5 or SHA-1 hashes.
What hashing means?
Hashing is the process of converting a given key into another value. A hash function is used to generate the new value according to a mathematical algorithm. ... A good hash function uses a one-way hashing algorithm, or in other words, the hash cannot be converted back into the original key.
Is SHA256 Crackable?
SHA-256 is a hashing function similar to that of SHA-1 or the MD5 algorithms. Hashing is a one way function – it cannot be decrypted back. ... However it can be cracked by simply brute force or comparing hashes of known strings to the hash.
Which is faster MD5 or SHA1?
MD5 can have 128 bits length of message digest. Whereas SHA1 can have 160 bits length of message digest. ... The speed of MD5 is fast in comparison of SHA1's speed. While the speed of SHA1 is slow in comparison of MD5's speed.
What is hash coding?
A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes.
Is SHA512 better than SHA256?
Either is fine. Note that SHA512 is a lot slower to compute than SHA256. In the context of secure hashing, this is an asset. Slower to compute hashes mean it takes more compute time to crack, so if you can afford the compute cost SHA512 will be more secure for this reason.
Which is better SHA1 or SHA256?
As SHA1 has been deprecated due to its security vulnerabilities, it is important to ensure you are no longer using an SSL certificate which is signed using SHA1. All major SSL certificate issuers now use SHA256 which is more secure and trustworthy.
Which hashing algorithm is the least secure?
SHA-1: A 160-bit hash function which resembles the earlier MD5 algorithm. This was designed by the National Security Agency (NSA) to be part of the Digital Signature Algorithm. Cryptographic weaknesses were discovered in SHA-1, and the standard was no longer approved for most cryptographic uses after 2010.
 Naneedigital
Naneedigital