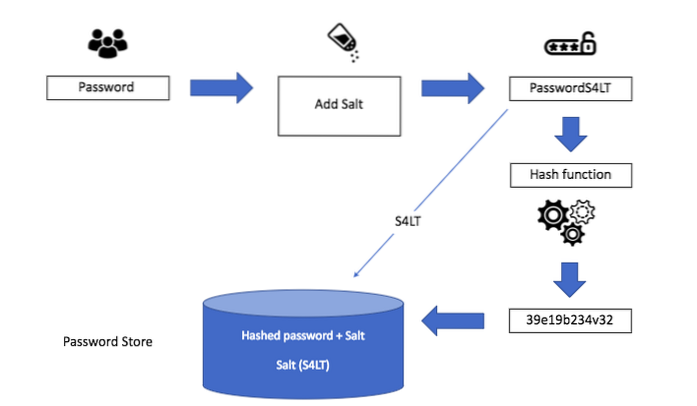
Hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, the hackers don't get access to your password. Instead, they just get access to the encrypted “hash” created by your password.
- What is password hash?
- What is hashing and how does it work?
- What is the purpose of hashing a password?
- How hashing is used in password protection?
- Is hashing password secure?
- What is hash and salt of a password?
- What is the purpose of hashing?
- What are the advantages of hashing?
- What is hashing used for?
What is password hash?
When a password has been “hashed” it means it has been turned into a scrambled representation of itself. A user's password is taken and – using a key known to the site – the hash value is derived from the combination of both the password and the key, using a set algorithm.
What is hashing and how does it work?
Hashing Function: The Core of Hashing Algorithm
A hash function is a mathematical function that converts an input value into a compressed numerical value – a hash or hash value. Basically, it's a processing unit that takes in data of arbitrary length and gives you the output of a fixed length – the hash value.
What is the purpose of hashing a password?
Hashing passwords provides defense against your passwords being compromised when a database has been compromised. It does this in two ways, 1. it hides the users passwords by making it computationally impossible to get the password from the hash, and 2.
How hashing is used in password protection?
Hashing performs a one-way transformation on a password, turning the password into another String, called the hashed password. ... “One-way” means that it is practically impossible to go the other way - to turn the hashed password back into the original password.
Is hashing password secure?
It's important to note that we never store the cleartext password in the process, we hash it and then forget it. Whereas the transmission of the password should be encrypted, the password hash doesn't need to be encrypted at rest. When properly implemented, password hashing is cryptographically secure.
What is hash and salt of a password?
A cryptographic salt is made up of random bits added to each password instance before its hashing. Salts create unique passwords even in the instance of two users choosing the same passwords. Salts help us mitigate hash table attacks by forcing attackers to re-compute them using the salts for each user.
What is the purpose of hashing?
Hashing is used to index and retrieve items in a database because it is faster to find the item using the shorter hashed key than to find it using the original value. It is also used in many encryption algorithms.
What are the advantages of hashing?
Advantages of Hashing
The main advantage of hash tables over other data structures is speed . The access time of an element is on average O(1), therefore lookup could be performed very fast. Hash tables are particularly efficient when the maximum number of entries can be predicted in advance.
What is hashing used for?
Hashing is a one-way function where data is mapped to a fixed-length value. Hashing is primarily used for authentication. Salting is an additional step during hashing, typically seen in association to hashed passwords, that adds an additional value to the end of the password that changes the hash value produced.
 Naneedigital
Naneedigital