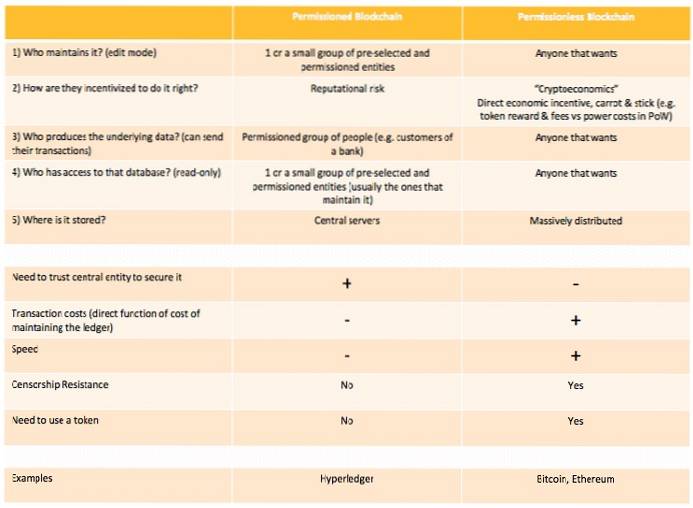
The basic distinction of these is clear from the terms itself. A permissioned blockchain needs prior approval before using whereas a permissionless blockchain lets anyone participate in the system. Though the two systems might sound similar, they cannot be used for the same things.
- What is a Permissionless Blockchain?
- What is decentralized Blockchain?
- What does Permissionless mean?
- How are private and public Blockchains different?
- Which Blockchain is the best?
- How many types of Blockchain are there?
- Can the Blockchain be hacked?
- What is an example of decentralization?
- What are the advantages of decentralization?
- Is it possible to have a private Permissionless network?
- How does a private Blockchain work?
- Which of the following best describes a Permissioned Blockchain?
What is a Permissionless Blockchain?
Permissionless blockchains are blockchains that require no permission to join and interact with. They are also known as public blockchains. Most of the time, permissionless blockchain is ideal for running and managing digital currencies.
What is decentralized Blockchain?
In blockchain, decentralization refers to the transfer of control and decision-making from a centralized entity (individual, organization, or group thereof) to a distributed network.
What does Permissionless mean?
Permisionless is a positive quality, where anyone is permitted to join and participate in an activity. Permissionless is oftne used when describing blockchain technologies because anyone can download the digital record known as the blockchain and participate in recording and verifying information.
How are private and public Blockchains different?
The most important difference is the role of the user on the network and how the identity is managed. In a private blockchain, the creator of the network knows from the beginning who the participants are. On a public network, you can't build a permission-based solution and the users have all guarantees of anonymity.
Which Blockchain is the best?
Ethereum is the best secure block chain based secure crypto currency platform. I helps to develop secure transparent crypto currency ... We have been looking for a high performance blockchain platform that could offer both private data storage as well as public ...
How many types of Blockchain are there?
Currently, there are at least four types of blockchain networks — public blockchains, private blockchains, consortium blockchains and hybrid blockchains.
Can the Blockchain be hacked?
The bitcoin network is underpinned by the blockchain technology, which is very difficult to hack. ... There have been instances of exchanges or wallets being hacked, but not the entire network. Having said that, there does exist potential security risks in various stages of the Bitcoin trading process.
What is an example of decentralization?
Example of Decentralisation
Good examples of decentralised business are Hotels, supermarket, Dress showrooms and etc. Because it is not possible for one person to focus on more than 100 branches which have branches throughout the world, take an example of a hotel.
What are the advantages of decentralization?
Advantages and Disadvantages Of Decentralisation
- Motivation of Subordinates. ...
- Growth and Diversification. ...
- Quick Decision Making. ...
- Efficient Communication. ...
- Ease of Expansion. ...
- Better Supervision And Control. ...
- Satisfaction of Human needs. ...
- Relief to top executives.
Is it possible to have a private Permissionless network?
Similar to the public permissionless network, anyone can spin up a node to join a private permissionless network. However, unlike on a public blockchain, other nodes will only acknowledge its existence, but not share any data.
How does a private Blockchain work?
A private blockchain is a special type of blockchain technology where only a single organization has authority over the network. So, it means that it's not open for the public people to join in.
Which of the following best describes a Permissioned Blockchain?
What Is a Permissioned Blockchain? Permissioned blockchains can be seen as an additional blockchain security system, as they maintain an access control layer to allow certain actions to be performed only by certain identifiable participants. For this reason, these blockchains differ from public and private blockchains.
 Naneedigital
Naneedigital