- How do you find out what rundll32 exe is running?
- What is rundll32 Exe used for?
- What is Windows host rundll32?
- How can I tell what is using svchost exe?
- How do I stop rundll32 exe from running?
- How do I use rundll32 Exe?
- Is rundll32 exe a virus?
- What does RuntimeBroker EXE do?
- What is Rundll?
- How do I fix Windows Host Process rundll32?
- What is Windows Host Process?
- Is Host Process for Windows Services a virus?
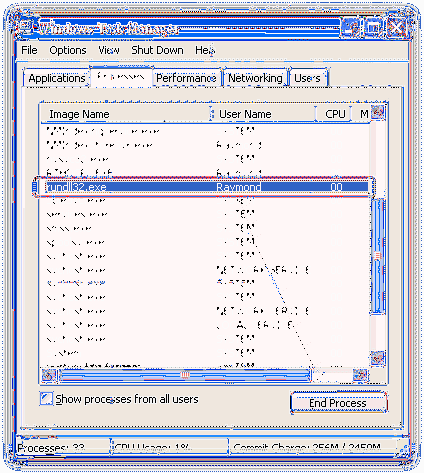
How do you find out what rundll32 exe is running?
Use Task Manager to Identify the Rundll32.exe Command in Use
Open Task Manager -> View menu -> Select Columns…, click the Command line box and then OK. A new column will now be available and you should be able to identify which dll is being executed.
What is rundll32 Exe used for?
Rundll32.exe allows users to trigger a function exported from a 32 bit DLL. It is written to exclusively trigger functions from those DLL's that are explicitly written to be called by it. Rundll was originally designed to be used internally at Microsoft, but is now available for generic use.
What is Windows host rundll32?
If you ever use Windows Task Manager to view the processes that are running on your computer, you may see the rundll32 process. ... Rundll32.exe is a critical Windows process that launches other 32-bit DLLs that reside on your computer.
How can I tell what is using svchost exe?
At the command prompt type tasklist /svc /fi "imagename eq svchost.exe" and press the enter key. You will see a list of the processes on your computer as well as the services that a SVCHOST.
How do I stop rundll32 exe from running?
In general, processes running on rundll32.exe can be stopped from running when Windows starts up as follows:
- Press Windows + R keys together to open the run dialog.
- Type msconfig and hit enter.
- On the Startup Tab will be a list of processes that start with Windows.
- Check the box marked Hide all Microsoft Services'
How do I use rundll32 Exe?
How to use the rundll32.exe file in Windows
- Shutdown, restart, logoff, or poweroff the computer. ...
- Lock the Windows 2000 and Windows XP workstation. ...
- Run the install for an inf file. ...
- Open the "Open with" folder for a file. ...
- Run copy disk program. ...
- Create a new shortcut. ...
- Open the screen saver window.
Is rundll32 exe a virus?
Rundll32.exe is a program used to run program code in DLL files which is part of Windows components. There are viruses that uses this name also that's why it's commonly mistaken as a real virus. There are also times that the file gets replaced with a malware infected one.
What does RuntimeBroker EXE do?
The genuine RuntimeBroker.exe file is a software component of Microsoft Windows by Microsoft. ... Runtime Broker is a Windows core process that helps manage apps and permissions for the Microsoft Store on Windows PCs. It checks apps for their respective permissions to ensure that they do not breach the end user's privacy.
What is Rundll?
1What is a Rundll File? ... Rundll and its later versions called Rundll 32 are a part of a vast network of code and data shared by many programs on your computer, which help to produce speed and memory efficiency in your operating system by reusing the same code or files when they run many functions by various programs.
How do I fix Windows Host Process rundll32?
Type “sfc /scannow” and press “Enter.” Windows will scan all your system files (including Rundll32) and repair any damaged files. Reboot your computer when the scan is complete.
What is Windows Host Process?
What Is It and Why Are There So Many in Task Manager? Host Process for Windows Tasks is an official Microsoft core process. In Windows, services that load from executable (EXE) files are able to institute themselves as full, separate processes on the system and are listed by their own names in Task Manager.
Is Host Process for Windows Services a virus?
Is svchost.exe a virus? No, it is not. The true svchost.exe file is a safe Microsoft Windows system process, called "Host Process". However, writers of malware programs, such as viruses, worms, and Trojans deliberately give their processes the same file name to escape detection.
 Naneedigital
Naneedigital