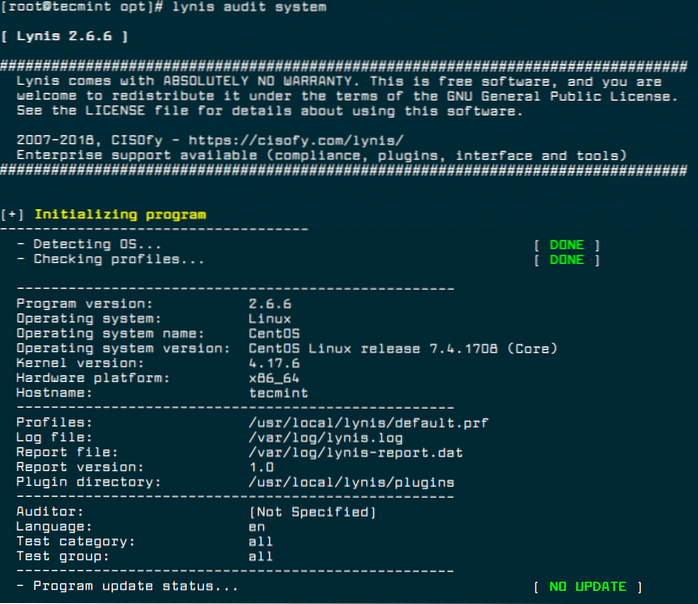
5 Tools to Scan a Linux Server for Malware and Rootkits
- Lynis – Security Auditing and Rootkit Scanner. Lynis is a free, open source, powerful and popular security auditing and scanning tool for Unix/Linux like operating systems. ...
- Chkrootkit – A Linux Rootkit Scanners. ...
- ClamAV – Antivirus Software Toolkit. ...
- LMD – Linux Malware Detect.
- Can Rootkits be detected?
- How do I scan for malware on Ubuntu?
- What is rootkit scan?
- Does ClamAV Scan for Linux viruses?
- How do I manually remove rootkit virus?
- What is the best rootkit removal tool?
- How do I scan my server for malware?
- How do I check for viruses on Ubuntu?
- Do we need antivirus for Ubuntu?
- What is the most dangerous type of rootkit?
- How long does a rootkit scan take?
- Can a rootkit infect the BIOS?
Can Rootkits be detected?
A surefire way to find a rootkit is with a memory dump analysis. You can always see the instructions a rootkit is executing in memory, and that is one place it can't hide. Behavioral analysis is one of the other more reliable methods of detecting rootkits.
How do I scan for malware on Ubuntu?
Scan Ubuntu Server for Malware and Rootkits
- ClamAV. ClamAV is a free and versatile open-source antivirus engine to detect malware, viruses, and other malicious programs and software on your system. ...
- Rkhunter. Rkhunter is the commonly used scanning option to check your Ubuntu server's general vulnerabilities and rootkits. ...
- Chkrootkit.
What is rootkit scan?
A rootkit is a clandestine computer program designed to provide continued privileged access to a computer while actively hiding its presence. ... Today rootkits are generally associated with malware – such as Trojans, worms, viruses – that conceal their existence and actions from users and other system processes.
Does ClamAV Scan for Linux viruses?
ClamAV does detect viruses for all platforms. It does scan for Linux viruses as well.
How do I manually remove rootkit virus?
How to remove rootkit malware. To clean up rootkits, you have several options. You can run the Windows Defender offline scan from inside Windows 10. Go to the Windows Defender Security Center, into Advanced scans and check the radius box to enable the Windows Defender offline scan.
What is the best rootkit removal tool?
It has a user-friendly graphical interface that is accessible for non-technical users.
- GMER. GMER is a rootkit scanner for experienced users. ...
- Kaspersky TDSSKiller. ...
- Malwarebytes Anti-Rootkit Beta. ...
- McAfee Rootkit Remover. ...
- Norton Power Eraser. ...
- Sophos Virus Removal Tool. ...
- Trend Micro Rootkit Buster.
How do I scan my server for malware?
5 Tools to Scan a Linux Server for Malware and Rootkits
- Lynis – Security Auditing and Rootkit Scanner. Lynis is a free, open source, powerful and popular security auditing and scanning tool for Unix/Linux like operating systems. ...
- Chkrootkit – A Linux Rootkit Scanners. ...
- ClamAV – Antivirus Software Toolkit. ...
- LMD – Linux Malware Detect.
How do I check for viruses on Ubuntu?
Scan Ubuntu 18.04 For Viruses With ClamAV
- Distributions.
- Introduction.
- Install ClamAV.
- Update The Threat Database.
- Command Line Scan. 9.1. Options. 9.2. Run The Scan.
- Graphical Scan. 10.1. Install ClamTK. 10.2. Set The Options. 10.3. Run The Scan.
- Closing Thoughts.
Do we need antivirus for Ubuntu?
No, you do not need an Antivirus (AV) on Ubuntu to keep it secure. You need to employ other "good hygiene" precautions, but contrary to some of the misleading answers and comments posted here, Anti-virus is not among them.
What is the most dangerous type of rootkit?
A kernel-level rootkit is considered most dangerous because it infects the core of a system.
How long does a rootkit scan take?
How Long Does a Rootkit Scan Take? Rootkit scans only search through the vital files on your computer. This helps speed up the process and makes it the optimal daily background scan. Most users should see the scan complete in less than 15 minutes.
Can a rootkit infect the BIOS?
Firmware and hardware
A firmware rootkit uses device or platform firmware to create a persistent malware image in hardware, such as a router, network card, hard drive, or the system BIOS.
 Naneedigital
Naneedigital