Using NGINX to prevent DDoS Attacks
- Nginx worker connections. ...
- Limiting requests rate. ...
- Limiting number of connections. ...
- Timeout parameters. ...
- Limit requests size. ...
- Blacklist IP adresses. ...
- Whitelist IP adresses. ...
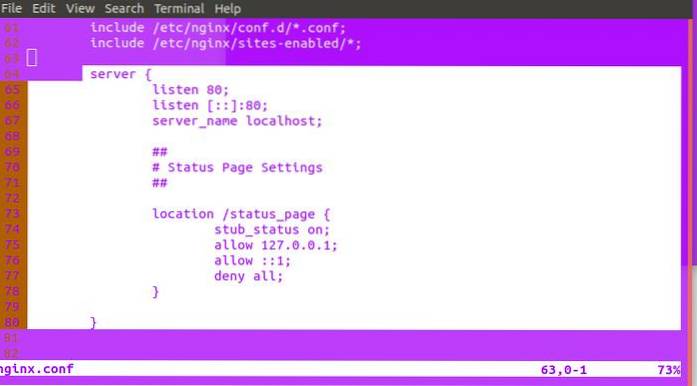
- Blocking access to a file or location.
- How can DDoS attacks be prevented?
- Can a firewall stop a DDoS attack?
- Can a VPN stop DDoS?
- Which DDoS attack is hardest to defend against?
- Is DDoS illegal?
- Can a DDoS attack be traced?
- What is the strongest DDoS method?
- What is the best DDoS protection?
- Is DDoS a virus?
- Does NordVPN stop DDoS?
- Can DDoS attacks steal information?
- Can a VPN protect you from hackers?
How can DDoS attacks be prevented?
Equip your network, applications, and infrastructure with multi-level protection strategies. This may include prevention management systems that combine firewalls, VPN, anti-spam, content filtering and other security layers to monitor activities and identity traffic inconsistencies that may be symptoms of DDoS attacks.
Can a firewall stop a DDoS attack?
Almost every modern firewall and intrusion prevention system (IPS) claims some level of DDoS defense. Some Unified Threat Management (UTM) devices or next-generation firewalls (NGFWs) offer anti-DDoS services and can mitigate many DDoS attacks.
Can a VPN stop DDoS?
Generally speaking, yes, VPNs can stop DDoS attacks. A primary benefit of a VPN is that it hides IP addresses. With a hidden IP address, DDoS attacks can't locate your network, making it much harder to target you.
Which DDoS attack is hardest to defend against?
Layer 7 attacks are some of the most difficult attacks to mitigate because they mimic normal user behavior and are harder to identify.
Is DDoS illegal?
DDoS attacks are illegal under the Computer Fraud and Abuse Act. Starting a DDoS attack against a network without permission is going to cost you up to 10 years in prison and up to a $500,000 fine.
Can a DDoS attack be traced?
A botnet is the network of bots. Without a botnet, the attack is just a DoS, which is weak, much easier to stop, and can be traced back.
What is the strongest DDoS method?
DNS Flood. One of the most well-known DDoS attacks, this version of UDP flood attack is application specific – DNS servers in this case. It is also one of the toughest DDoS attacks to detect and prevent.
What is the best DDoS protection?
Best DDoS protection of 2021
- Project Shield.
- Cloudflare.
- AWS Shield.
- Microsoft Azure.
- Verisign DDoS Protection/ Neustar.
Is DDoS a virus?
DDoS is a malicious network attack in which hackers overwhelm a website or service with false web traffic or requests from numerous enslaved Internet-connected devices.
Does NordVPN stop DDoS?
NordVPN can help protect you from DDoS and other attacks. Try it now with a 30-day money-back guarantee.
Can DDoS attacks steal information?
DDoS attacks cannot steal website visitors information. The sole purpose of a DDoS attack is to overload the website resources. However, DDoS attacks can be used as a way of extortion and blackmailing. For example, website owners can be asked to pay a ransom for attackers to stop a DDoS attack.
Can a VPN protect you from hackers?
Essentially, a VPN makes a type of tunnel that prevents hackers, snoopers, and internet service providers (ISPs) from looking at your instant messages, the browsing history, credit card information, downloads, or anything that you send over a network.
 Naneedigital
Naneedigital