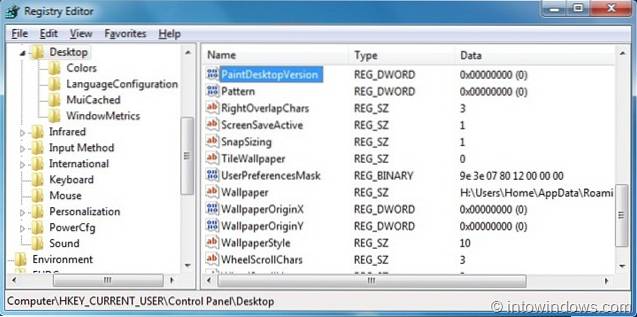
To make your MacBook invisible on the network, turn off the Sharing function in the MacBook System Preferences panel.
- Click on the "System Preferences" icon in the MacBook dock to open the System Preferences window.
- Click on the icon labeled "Sharing" in the "Internet and Wireless" category.
- How do I hide my computer on a network?
- How do I hide a device from my WiFi?
- Can you mask your MAC address?
- How do I protect my computer from network administrator?
- How can I hide my network?
- Can 2 devices have same MAC address?
- Why is it important to disable WiFi and Bluetooth when you are not using them?
- Can you be tracked using public WiFi?
- Does Tor hide MAC address?
- Is spoofing your MAC address illegal?
- Can MAC spoofing be detected?
How do I hide my computer on a network?
How to Hide a Computer From the Other Computers on the Network
- Right-click the network or Wi-Fi icon in the system tray area of the Windows taskbar and select "Open Network and Sharing Center."
- Click the "Change advanced sharing settings" link in the left pane.
- Select the "Turn off network discovery" option. ...
- Click the "Save changes" button.
How do I hide a device from my WiFi?
Hover over the Wireless menu item, and select the Advanced submenu. Find the line that says “Hide SSID (Closed Network)” and change the dropdown to say “Enabled”. Click Save on the same row on the right hand side. Your wireless network has now been hidden.
Can you mask your MAC address?
All MAC addresses are hard-coded into a network card and can never be changed. However, you can change or spoof the MAC address in the operating system itself using a few simple tricks. ... If you can sniff out a legitimate MAC address, you can then spoof your MAC address and gain access to the WiFi network.
How do I protect my computer from network administrator?
In Windows, right-click the folder, go to Properties, and open the Security tab. Then click the Edit button. You can then select a group or user name and choose to deny access to the folder. Someone trying to access it will be required to put in an administrator password.
How can I hide my network?
Tap Connect and wait for your Android device to establish a connection.
...
- Open the system menu.
- Click the WiFi icon and go to WiFi settings.
- Press the menu button in the top-right corner of the window and select Connect to Hidden Network.
- Add a new hidden network.
- Enter the required information.
- Click Connect.
Can 2 devices have same MAC address?
In order for a network device to be able to communicate, the MAC Address it is using must be unique. ... If two devices have the same MAC Address (which occurs more often than network administrators would like), neither computer can communicate properly. On an Ethernet LAN, this will cause a high number of collisions.
Why is it important to disable WiFi and Bluetooth when you are not using them?
Turn Bluetooth off when not in use. Keeping it active enables hackers to discover what other devices you connected to before, spoof one of those devices, and gain access to your device. ... This prevents other unknown devices from finding your Bluetooth connection.
Can you be tracked using public WiFi?
Oh yes, absolutely it can. Unless you are using a VPN, your identity can easily be guessed through the IP address assigned to your device. You see, when you connect to a public Wifi without using a VPN, it means that your data is almost transparent to the hackers and cyber-criminals.
Does Tor hide MAC address?
3 Answers. The MAC address is only visible on your local network. You don't need to hide it. With Tor or without Tor, as soon as the packet reaches your default gateway, that computer sitting between you and the next network segment, your MAC cannot be seen anymore.
Is spoofing your MAC address illegal?
While this is generally a legitimate case, MAC spoofing of new devices can be considered illegal if the ISP's user agreement prevents the user from connecting more than one device to their service. Moreover, the client is not the only person who can spoof their MAC address to gain access to the ISP.
Can MAC spoofing be detected?
Unfortunately, MAC address spoofing is hard to detect. Most current spoofing detection systems mainly use the sequence number (SN) tracking technique, which has drawbacks. Firstly, it may lead to an increase in the number of false positives.
 Naneedigital
Naneedigital