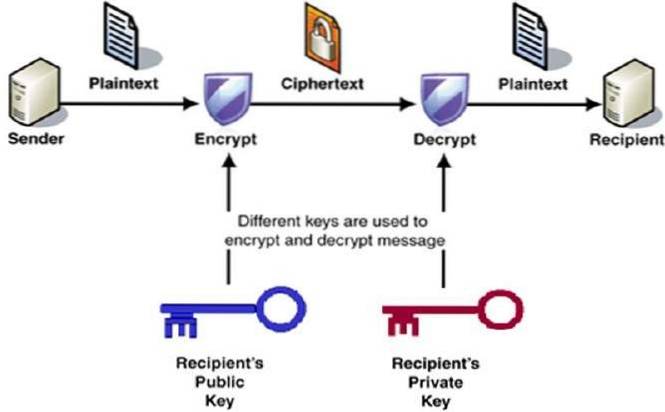
To recap: Public key cryptography allows someone to send their public key in an open, insecure channel. Having a friend's public key allows you to encrypt messages to them. Your private key is used to decrypt messages encrypted to you.
- How does public key asymmetric encryption work?
- How does RSA public key encryption work?
- How does public key encryption work quizlet?
- How do I encrypt a message with a public key?
- How do you generate a public key?
- Which is the principle of the encryption using a key?
- Can you decrypt with a public key?
- How do I read an encrypted message?
- What is the difference between private key and public key?
- What is meant by public key encryption?
- Can private key be derived from public key?
- What cryptography uses two keys a private and a public key?
How does public key asymmetric encryption work?
Asymmetric Encryption uses two distinct, yet related keys. One key, the Public Key, is used for encryption and the other, the Private Key, is for decryption. As implied in the name, the Private Key is intended to be private so that only the authenticated recipient can decrypt the message.
How does RSA public key encryption work?
Under RSA encryption, messages are encrypted with a code called a public key, which can be shared openly. Due to some distinct mathematical properties of the RSA algorithm, once a message has been encrypted with the public key, it can only be decrypted by another key, known as the private key.
How does public key encryption work quizlet?
How does public Key Encryption work? Mathematical Algorithms are used to create two separate keys for the encryption/decryption process. One key is private (used to decrypt) and the other is public (used to encrypt). You cannot decrypt the message using the key that was used to encrypt it.
How do I encrypt a message with a public key?
- Install GPG. First, GPG must be installed. ...
- Generate your public and private keys. The first thing we'll do is generate a pair of keys. ...
- Export your public key. ...
- Exchange public keys with Alice. ...
- Import Alice's public key. ...
- Review the keys in your keyring. ...
- Encrypt the message you want to send. ...
- Decrypt message you've received.
How do you generate a public key?
How to Create a Public/Private Key Pair
- Start the key generation program. myLocalHost% ssh-keygen Generating public/private rsa key pair. ...
- Enter the path to the file that will hold the key. ...
- Enter a passphrase for using your key. ...
- Re-enter the passphrase to confirm it. ...
- Check the results. ...
- Copy the public key and append the key to the $HOME/.
Which is the principle of the encryption using a key?
Discussion Forum
| Que. | Which is the principle of the encryption using a key? |
|---|---|
| b. | The key contains the secret function for encryption including parameters. Only a password can activate the key |
| c. | All functions are public, only the key is secret. It contains the parameters used for the encryption resp. decryption |
Can you decrypt with a public key?
Yes, a message which has encrypted using private key can be decrypted using the public key. ... In the digital signature, a person encrypts the hash of the data with his private key. Anyone can decrypt the same with the available public key of the person and verify the authenticity of the data.
How do I read an encrypted message?
How to Read Encrypted Text Messages Through Textpad
- Launch TextPad and open the encrypted message in the program.
- Select the entire text of the message by pressing the "Ctrl-A" keys. ...
- Open the appropriate encryption software. ...
- Enter the passphrase or password that was originally used to encrypt the message.
- Click the "Decrypt" button.
What is the difference between private key and public key?
Private Key is used to both encrypt and decrypt the data and is shared between the sender and receiver of encrypted data. The public key is only used to encrypt data and to decrypt the data, the private key is used and is shared. ... The public key is free to use and the private key is kept secret only.
What is meant by public key encryption?
Public key encryption is a form of encryption that uses two keys. A public key, which everyone knows, and a private key, which only you know. To encrypt, the public key is applied to the target information, using a predefined operation (several times), to produce a pseudo-random number.
Can private key be derived from public key?
The public key is derived from the private key at generation time, and with the private key at any point in the future it is possible to re-derive the public key easily. It is not feasible to go the other way. Given a public key it is not easy to derive the private key.
What cryptography uses two keys a private and a public key?
(also known as public key encryption) uses two keys that are mathematically related. Both keys together are called the key pair. The public key is made available to anyone; the private key is kept secret.
 Naneedigital
Naneedigital