- How can hackers be traced or identified?
- How does hackers get caught?
- How do hackers remain anonymous?
- What information do hackers look for?
- Does netstat show hackers?
- Can you find out who hacked your email?
- Do hackers go to jail?
- How do hackers hide their IP?
- Where do hackers learn to hack?
- Can you be tracked on Tor?
- Which VPN do hackers use?
- How can I hide my identity online?
How can hackers be traced or identified?
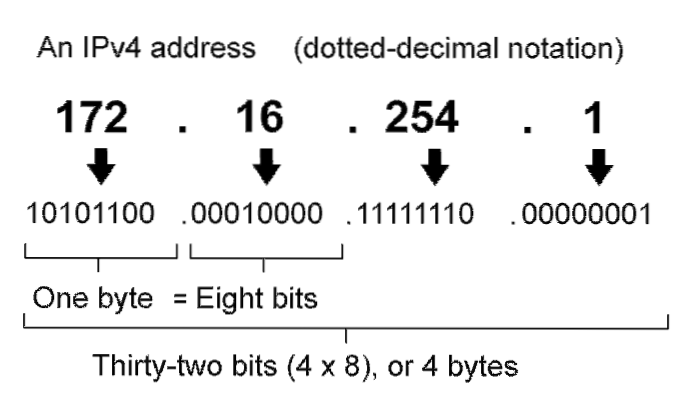
The first step to identify a hacker is to trace the IP address of the intruder. ... The other method of tracing a hacker is by using Domain Name Server (DNS). DNS are machines that are connected to internet that keeps track of IP addresses and Domain Names of other PCs.
How does hackers get caught?
Hackers will often use secure software such as a proxy server to hide their identity and funnel their communications through lots of different countries in order to evade detection. ... The combination of these tools allows them to commit their crimes undetected and in countries where they know they can't be prosecuted.
How do hackers remain anonymous?
Instead, use anonymous email services or remailers. Anonymous email services allow you to email someone without any trace back to you, especially if coupled with VPN or TOR access. Remailers are a service whereby you can send from a real email account and the remailer will forward it on anonymously.
What information do hackers look for?
Skilled hackers could gain access to the following: Your credit card numbers. Your bank account. Your Social Security number.
Does netstat show hackers?
If the malware on our system is to do us any harm, it needs to communicate to the command and control center run by the hacker. ... Netstat is designed to identify all connections to your system. Let's try using it to see whether any unusual connections exist.
Can you find out who hacked your email?
The short answer is, you're extremely unlikely to figure out who hacked your email account. There's almost nothing you can do.
Do hackers go to jail?
Hacking (or more formally, “unauthorized computer access”) is defined in California law as knowingly accessing any computer, computer system or network without permission. ... It's usually a misdemeanor, punishable by up to a year in county jail.
How do hackers hide their IP?
TOR- The Onion Router is another popular method used by cyber-criminals to hide their tracks. The Tor network in simpler terms sounds like a proxy on steroids. The network will bounce your connection across multiple points to provide a high degree of anonymity.
Where do hackers learn to hack?
Short answer: by self-teaching and through private forums, but nowadays there are publicly available courses thanks to the rise of pen-testing (legal hacking). Long answer: being a “hacker” requires knowledge from many IT subfields.
Can you be tracked on Tor?
While Tor provides a much higher level of anonymity than a regular web browser, it's not 100% secure. Your location will be hidden and your traffic can't be tracked, but certain people can still see your browsing activity – at least part of it.
Which VPN do hackers use?
NordVPN stops DNS spoofing attacks (we also stop DNS leaks! When using NordVPN or any other VPN, use our free DNS leak test to make sure you're secure). As your DNS signal travels from NordVPN's DNS server through your encrypted tunnel, it's virtually impossible for hackers to corrupt that signal in any way.
How can I hide my identity online?
First, you can use a virtual private network (VPN). For most intents and purposes, a VPN obscures your IP address, and a proxy does the same — and in some cases, even better. A VPN is a private, encrypted network that “tunnels” through a public network (usually the internet) to connect remote sites or users.
 Naneedigital
Naneedigital