- How do I verify integrity of a downloaded file?
- How is a hash algorithm used in checking the integrity of a file?
- How do you ensure file integrity?
- Does hash algorithm provide integrity?
- How does file verification work?
- How do I find the hash value of a file?
- What is the purpose of file hashing?
- What is the purpose of hashing?
- What are the different types of hashing techniques?
- What is integrity verification?
- What does integrity mean?
- Is used to verify the integrity of a message?
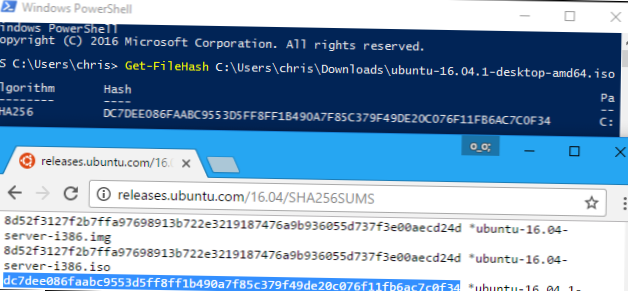
How do I verify integrity of a downloaded file?
Verify in the Internet
The service is easy to use. Just drag & drop the respective file to the drop zone in the webpage or open the file dialog. Then choose SHA256 or MD5 as checksum type, insert the checksum from the file you got from download webpage. Finally click on [Compare] to start the verification.
How is a hash algorithm used in checking the integrity of a file?
Cryptographic Hash Function algorithm works by comparing the file's original and current hash values. And if a byte or even a piece of the file's data has been changed, the original and current hash values will be different, and therefore you will know whether it's the same file or not.
How do you ensure file integrity?
Data Integrity Follow Up: Ways to Protect Your Data
- Backups. Perhaps the easiest way to keep a clean copy of your data. ...
- Maintenance. Always a good idea to ensure your storage media is acting as it should. ...
- Audit. Worth a manual check every so often. ...
- Timestamping. About as straightforward as it gets. ...
- Limit Access. ...
- Digital Signatures. ...
- Cyclic Redundancy Checks. ...
- Salting.
Does hash algorithm provide integrity?
A hash function does not provide integrity! posted April 2017. ... A hash function does not provide integrity, a MAC provides integrity. Instead a cryptographic hash function provides three properties, well defined in the world of cryptography: collision resistance, pre-image resistance and second pre-image resistance.
How does file verification work?
File verification is the process of using an algorithm for verifying the integrity of a computer file. This can be done by comparing two files bit-by-bit, but requires two copies of the same file, and may miss systematic corruptions which might occur to both files.
How do I find the hash value of a file?
Right-click on a file or a set of files, and click Hash with HashTools in the context menu. This launches the HashTools program and adds the selected file(s) to the list. Next, click on a hashing algorithm (e.g., CRC, MD5, SHA1, SHA256, etc) to generate the hash checksum for the files.
What is the purpose of file hashing?
Hashing has a large number of applications in cybersecurity, centering around the ability to verify that data is legitimate. With a secure hashing algorithm, one could verify that a downloaded file matched what was expected. In fact, many projects provide hashes alongside their downloads.
What is the purpose of hashing?
Hashing is used to index and retrieve items in a database because it is faster to find the item using the shorter hashed key than to find it using the original value. It is also used in many encryption algorithms.
What are the different types of hashing techniques?
Data bucket, Key , Hash function, Linear Probing, Quadratic probing , Hash index, Double Hashing, Bucket Overflow are important terminologies used in hashing. Two types of hashing methods are 1) static hashing 2) dynamic hashing. In the static hashing, the resultant data bucket address will always remain the same.
What is integrity verification?
The IRS's Integrity and Verification Operation (IVO) function screens and verifies potentially fraudulent tax returns to prevent the issuance of improper refunds.
What does integrity mean?
The Random House Dictionary defines integrity as: Adherence to moral and ethical principles; soundness of moral character; honesty. The state of being whole, entire or undiminished.
Is used to verify the integrity of a message?
1 Answer. Explanation: Message Digest is a type of cryptographic hash function that contains a string of digits that are created by the one-way hashing formula. It is also known as a type of technique used for verifying the integrity of the message, data or media, and to detect if any manipulations are made.
 Naneedigital
Naneedigital