Beginner's Guide to nmap – Part 1
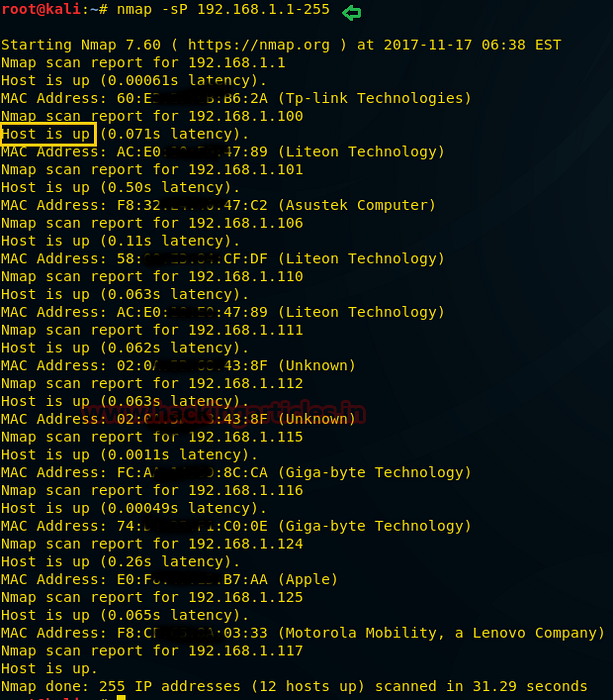
- Perform a Quick Ping Scan of a Network Subnet. ...
- Perform a SYN Scan of a Network Subnet. ...
- Perform a TCP Connect Scan of a Network Subnet. ...
- Scan a Specific Port, List of Ports, or Range of Ports on a Remote Host or Subnet. ...
- Banner Grabbing to Identify OS Version / Type and Service Version / Type. ...
- Speeding Up or Slowing Down Scans.
- Is it illegal to use nmap?
- How do I start nmap?
- Is Nmap easy to use?
- Do hackers use nmap?
- Can Nmap scans be detected?
- Why is port scanning dangerous?
- Why Nmap is not working?
- How long does Nmap take to scan all ports?
- How Hackers use open ports?
- What is Nmap typically used for?
- What is the difference between nmap and wireshark?
- What is nikto tool?
Is it illegal to use nmap?
Using Nmap is not exactly an illegal act since no federal law in the United States explicitly bans port scanning. Effective use of Nmap can protect your system network from intruders. However, unapproved port scanning for whatever reason can get you jailed, fired, disqualified, or even prohibited by your ISP.
How do I start nmap?
To get started, download and install Nmap from the nmap.org website and then launch a command prompt. Typing nmap [hostname] or nmap [ip_address] will initiate a default scan. A default scan uses 1000 common TCP ports and has Host Discovery enabled. Host Discovery performs a check to see if the host is online.
Is Nmap easy to use?
The process for installing Nmap is easy but varies according to your operating system. The Windows, Mac, and Linux versions of the program can be downloaded here.
Do hackers use nmap?
Nmap can be used by hackers to gain access to uncontrolled ports on a system. All a hacker would need to do to successfully get into a targeted system would be to run Nmap on that system, look for vulnerabilities, and figure out how to exploit them. Hackers aren't the only people who use the software platform, however.
Can Nmap scans be detected?
Usually only scan types that establish full TCP connections are logged, while the default Nmap SYN scan sneaks through. ... Intrusive scans, particularly those using Nmap version detection, can often be detected this way. But only if the administrators actually read the system logs regularly.
Why is port scanning dangerous?
How Dangerous Are Port Scans? A port scan can help an attacker find a weak point to attack and break into a computer system. ... Just because you've found an open port doesn't mean you can attack it. But, once you've found an open port running a listening service, you can scan it for vulnerabilities.
Why Nmap is not working?
RE: NMAP does not work
- You have to have L3 information (ARP) from some source - DHCP, SPAN port, Router etc. for NMAP to work. Again make sense becasue NMAP is IP based. - Obviously the firewall need to allow port scanning.
How long does Nmap take to scan all ports?
So the total time Nmap will spend scanning the network can be roughly extrapolated by multiplying 21 minutes per host by the number of hosts online. If version detection or UDP are being done as well, you'll also have to watch the timing estimates for those.
How Hackers use open ports?
Malicious ("black hat") hackers (or crackers) commonly use port scanning software to find which ports are "open" (unfiltered) in a given computer, and whether or not an actual service is listening on that port. They can then attempt to exploit potential vulnerabilities in any services they find.
What is Nmap typically used for?
Nmap, short for Network Mapper, is a free, open-source tool for vulnerability scanning and network discovery. Network administrators use Nmap to identify what devices are running on their systems, discovering hosts that are available and the services they offer, finding open ports and detecting security risks.
What is the difference between nmap and wireshark?
Both very handy tools, Nmap allows you to scan an object for listening ports, discover services on a network and more. Wireshark lets you log network traffic and analyse it. Both leverage winpcap to work on Windows.
What is nikto tool?
Nikto is a free software command-line vulnerability scanner that scans webservers for dangerous files/CGIs, outdated server software and other problems. It performs generic and server type specific checks. It also captures and prints any cookies received.
 Naneedigital
Naneedigital