Different Ways to Secure SSH Server
- By changing Default SSH Port.
- Using Strong Password.
- Using Public Key.
- Allowing a single IP to Log in.
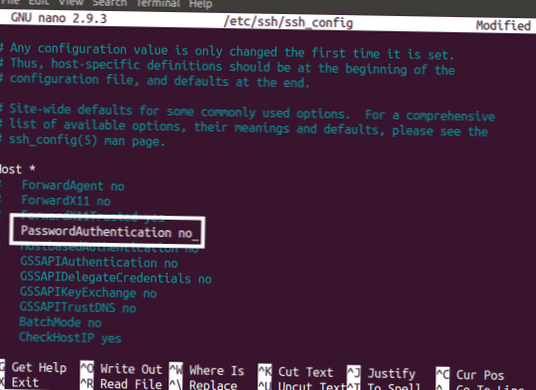
- Disabling Empty Password.
- Using Protocol 2 for SSH Server.
- By Disabling X11 Forwarding.
- Setting an Idle Timeout.
- How do you secure a Linux server?
- How secure is OpenSSH?
- Which SSH ciphers are secure?
- How do I protect my SSH key?
- How do you secure a server?
- How you secure your Windows and Linux server?
- Can SSH be hacked?
- Is port 22 secure?
- Should I change my SSH port?
- How do I know if TLS 1.2 is enabled on Linux?
- What is ciphers in ssh?
- What is KEX in SSH?
How do you secure a Linux server?
10 Security Best Practices for Linux Servers
- Use Strong and Unique Passwords. ...
- Generate an SSH Key Pair. ...
- Update Your Software Regularly. ...
- Enable Automatic Updates. ...
- Avoid Unnecessary Software. ...
- Disable Booting from External Devices. ...
- Close Hidden Open Ports. ...
- Scan Log Files with Fail2ban.
How secure is OpenSSH?
Conclusion. OpenSSH is the standard for secure remote access to *Unix-like servers, replacing the unencrypted telnet protocol. SSH (and its file transfer sub-protocol SCP) ensures that the connection from your local computer to the server is encrypted and secure.
Which SSH ciphers are secure?
The good. AES and ChaCha20 are the best ciphers currently supported. AES is the industry standard, and all key sizes (128, 192, and 256) are currently supported with a variety of modes (CTR, CBC, and GCM). ChaCha20 is a more modern cipher and is designed with a very high security margin.
How do I protect my SSH key?
4 Ways to Start Protecting Your SSH Keys
- Build an SSH Inventory. You can't protect something about which you don't know. ...
- Identify Vulnerabilities in Your SSH Environment. The next step to strong SSH key management is scanning an inventory for known vulnerabilities and issues. ...
- Remediate Known SSH Issues. ...
- Monitor Your SSH Keys for Additional Risks.
How do you secure a server?
Secure Server Connectivity
- Establish and Use a Secure Connection. ...
- Use SSH Keys Authentication. ...
- Secure File Transfer Protocol. ...
- Secure Sockets Layer Certificates. ...
- Use Private Networks and VPNs. ...
- Monitor Login Attempts. ...
- Manage Users. ...
- Establish Password Requirements.
How you secure your Windows and Linux server?
10 Easy Ways to Secure your Windows Server
- Install only required OS components. ...
- Keep the 'Admin' account secure. ...
- Setup User Account Policies. ...
- Employ the Principle of “Least Privilege“ ...
- Disable unnecessary network ports and services. ...
- Enable Windows Firewall and Antivirus. ...
- Use Windows BitLocker Drive Encryption.
Can SSH be hacked?
SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials.
Is port 22 secure?
An SSH server, by default, listens on the standard Transmission Control Protocol (TCP) port 22. ... Secure Shell provides strong authentication and encrypted data communications between two computers connecting over an open network such as the internet.
Should I change my SSH port?
Changing the port only stops automatic attacks against your SSH and some script kiddies. If someone was targeting you then they could fine the new SSH port. The advantage is that it stops failed login attempts in your logs.
How do I know if TLS 1.2 is enabled on Linux?
You should use openssl s_client, and the option you are looking for is -tls1_2. If you get the certificate chain and the handshake you know the system in question supports TLS 1.2. If you see don't see the certificate chain, and something similar to "handshake error" you know it does not support TLS 1.2.
What is ciphers in ssh?
SSH can be configured to utilize a variety of different symmetrical cipher systems, including AES, Blowfish, 3DES, CAST128, and Arcfour. The server and client can both decide on a list of their supported ciphers, ordered by preference.
What is KEX in SSH?
The kex-alg command specifies which KEX algorithms in the SSH client profile for SSH encryption negotiation with an SFTP server when the DataPower Gateway acts as an SFTP client. An SSH client profile is associated with an SFTP client policy. ... To specify multiple algorithms, run this command for each algorithm.
 Naneedigital
Naneedigital